The firm’s newly published research blueprint underscores the necessity for security leaders to discern between in-house and outsourced security functions, a critical step toward cost reduction, resource optimization, and overall security enhancement.
TORONTO, Sept. 28, 2023 /PRNewswire/ – In light of the growing frequency of cyberattacks, including the recent attack on several major Las Vegas casinos, the urgency for specialized security services has become starkly evident. However, the scarcity of skilled labor escalates the cost of implementing internal security measures, making the option of outsourcing a more attractive alternative to organizations already concerned with cutting costs in an uncertain economy. Organizations often also grapple with limited time and resources, further inhibiting their capacity to establish internal security systems. To address this pressing issue and support security leaders in ensuring robust business security, Info-Tech Research Group has published its Select a Security Outsourcing Partner research blueprint.
In the new resource, Info-Tech reports that IT leaders can face a host of complexities when selecting an appropriate outsourcing partner. With many service providers and technology tools available in this field, choosing the right security provider becomes particularly challenging. The firm advises that understanding one’s own internal security needs and comprehending the broader business environment are crucial steps before making a decision, as only with this in-depth knowledge can security leaders effectively select an outsourcing partner that aligns with their needs and help protect against the ever-evolving landscape of cyberthreats.
“We often recommend organizations outsource certain aspects of their information security portfolio to providers, recognizing that providers make it their business to be much more qualified to defend against attacks and keep organizations compliant,” says Fred Chagnon, principal research director at Info-Tech Research Group. “The challenge is that, often, these service providers achieve scale and profitability when their customers are as alike as possible, and this tendency toward sameness can result in a one-size-fits-most approach.”
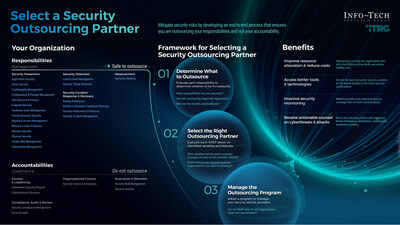
The firm’s blueprint highlights the importance for security leaders to understand which security functions can be effectively handled in-house and which should be outsourced. This process is key to achieving cost savings, optimizing resource allocation, and enhancing the overall security posture. It is equally crucial to consider the long-term financial implications of outsourcing versus insourcing to identify the most economical approach.
Info-Tech analysts suggest security leaders consider the following methodology to choose the right outsourcing partner to mitigate risk and potential attacks:
- Determine responsibilities. Consider the responsibilities that could potentially be outsourced to a service partner and analyze which tasks might be more efficiently handled externally compared to those best managed in-house. Based on these identified responsibilities, decide whether engaging a service partner is necessary.
- Scope requirements. Refine the list of role-based requirements, variables, and features required. Use a well-known list of critical security controls as a framework to determine these activities and send out requests for proposal (RFPs) to pick the best candidate for the organization.
- Manage the outsourcing program. Trust the managed security service providers (MSSPs), but verify their results to ensure the organization receives the promised service level.
The resource explains that although organizations have the option to outsource specific duties or entire functions, they cannot transfer accountability. If a data breach or hacking occurs, the organization’s security leaders are ultimately responsible. Consequently, it is critical to carefully choose a trustworthy MSSP as a collaborator and remember that outsourcing does not mean abandoning responsibility.
To learn more about organizational security needs and insights on choosing the right outsourcing partner, download the firm’s complete Select a Security Outsourcing Partner blueprint.
For media inquiries on the topic or to get exclusive, timely commentary from Fred Chagnon, an expert in IT infrastructure and operations, please contact [email protected].
Info-Tech Research Group is one of the world’s leading information technology research and advisory firms, proudly serving over 30,000 IT professionals. The company produces unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. For 25 years, Info-Tech has partnered closely with IT teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
Media professionals can register for unrestricted access to research across IT, HR, and software and over 200 IT and industry analysts through the firm’s Media Insiders program. To gain access, contact [email protected].
For more information about Info-Tech Research Group or to access the latest research, visit infotech.com and connect via LinkedIn and Twitter.
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/evaluating-security-outsourcing-in-the-wake-of-recent-high-profile-cyberattacks-info-tech-research-group-publishes-new-resource-301942222.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/evaluating-security-outsourcing-in-the-wake-of-recent-high-profile-cyberattacks-info-tech-research-group-publishes-new-resource-301942222.html
SOURCE Info-Tech Research Group

Featured image: Megapixl © Alexandersikov